With changes in technologies, many organizations are exploring newer deployment options that align with their Cloud strategy. When talking about Cloud Strategy, Azure is something that cannot be ignored. Most organizations are already using a few Microsoft cloud-based services like Office 365, hence Azure Active Directory is anyways part of the game. When talking about Citrix deployments to align with these modern directory services, sometimes we lack a bit of background. These strategies are definitely going to make a long-term impact on the architecture, hence it is essential to know about the options to leverage Azure Active Directory for Citrix Deployments. But before we really explore the options, here come the basics of what machine identity is and what options we have to make the right choices.
Identity in Azure Active Directory
When we talk about VDI identity, we basically mean the VDI Machine Account which gets created once devices are added to any directory services. There are two types of operations that are related to the device identity or computer account in Azure Active Directory:
- Registered – This is also called ‘Workplace Joined’. This is mainly for BYO devices, which utilize the services available from Azure, device management does not happen via Azure InTune. In this scenario, users can use their mobile and other devices to access corporate-related services like O365 without managing the device from corporate. These are generally not related to VDI operations.
- Join – This is more relevant for VDIs as these devices require Directory Service management. These are primarily for Corp-owned devices or VDIs where management also happens via the Identity Provider. These devices could be Win10, Win 11 Client OS VDIs or Windows Server 2019 and new OS based Hosted Shared Servers. Devices can be joined to AD, Azure AD, or to both (Hybrid).
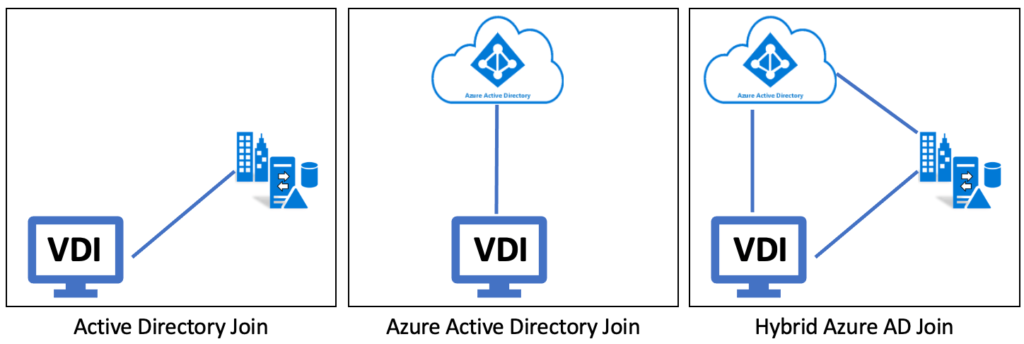
VDI Machine Identity on Active Directory, Azure Active Directory, or Hybrid Azure Active Directory
In the case of the Join operation, there are three main places where VDI machine account identity can stay. However please note that Citrix also supports Non-Domain Join VDIs as well. In any organization, one or more types of configurations can also co-exist.
- Active Directory (AD)
- Azure Active Directory (AAD)
- Hybrid Azure Active Directory (H-AAD)
Active Directory
This is the traditional configuration where machine Identity is stored and managed from On-Prem AD DS (Active Directory Domain Services) or Azure AD Domain Services (Azure AD DS). In this case, all the group policies and machine management happen from Active Directory itself.
Azure Active Directory
This is the configuration where entire VDI management can be done using Azure Active Directory through tools like Intune. This is part of the configuration where VDI account details are part of AAD and there is no dependency or requirement of AD DS. This also means that there would not be any Group Policies etc for VDI management. This configuration requires Rendezvous V2 to be enabled. There are multiple limitations to this configuration, which can be reviewed here.
Hybrid Azure Active Directory
This is the configuration that keeps VDI identity in Active Directory and also syncs that with Azure AD. The VDI can be managed through Intune and similarly, Group Policies can be applied through On-Prem AD DS. Many organizations consider this as an interim step before going to complete Azure Active Directory Join as this allows support for down-level Windows versions as well. There are a few limitations that can be reviewed here.
Things to consider before choosing the right Directory Join for Citrix Deployment
| Parameter | Active Directory | Azure Active Directory | Hybrid Azure Active Directory |
| Citrix Offering | DaaS or CVAD | Only Citrix DaaS | Only Citrix DaaS |
| VDA Type | Any | Single Session (Desktop Only) or Multi-Session (Apps and Desktops) | Single Session (Desktop Only) or Multi-Session (Apps and Desktops) |
| VDA Version | Any | 2203 or later | 2112 or later |
| Provisioning Type | Any | MCS | MCS |
| FlexCast Model | Any | Persistent and Non-Persistent using Machine Profile Workflow | Persistent and Non-Persistent |
| Assignment Type | Any | Dedicated and Pooled | Dedicated and Pooled |
| Hosting Platform | Any | Azure Only | Any hypervisor or Cloud |
| Image Prep | NA | Master VMs must not be joined to Azure AD | Master VMs must not be joined to Azure AD. Master VM can be AD joined or non-domain joined. |
| Workspace Identity Providers (AAD, AD, Okta, SAML, Citrix Gateway, Adaptive Auth) | All are Supported | Only AAD is supported | All are Supported |
| Note | NA | Rendezvous V2 must be enabled | NA |
Conclusion
With modern innovations, there are multiple options that organizations can choose for VDI identity management, however, these decisions are crucial and must consider long-term scenarios while making any decisions. With Azure gaining a lot of popularity, many organizations are considering Hybrid Azure Active Directory to allow them to feel the modern management without jeopardizing the legacy infrastructure they have.
In the comments, do let me know what are you proposing to your customers and what is the rationale behind that.