As we saw at the beginning “Introduction to Citrix Cloud” Virtual Apps and Desktop delivery has been a forte for Citrix. We also saw how Citrix DaaS ensures a “superior experience for End Users as well as Admins“. However, for the most environment, only user experience is not the criteria. For most organizations, compliance with industry regulations, safeguarding information, and protecting internal assets are other big challenges. We can look at security from a standalone viewpoint, however, if we do so, we are creating a multi-fold challenge to balance user experience and security. Citrix helps in maintaining this ‘Zen’ between security and user experience. Citrix DaaS applies security controls, ensuring that the user experience is not degraded. Hence you’d find security is the second most prominent pillar in all the Citrix documentation. Let’s have a close look at how Citrix provides required security controls, without compromising on user experience.
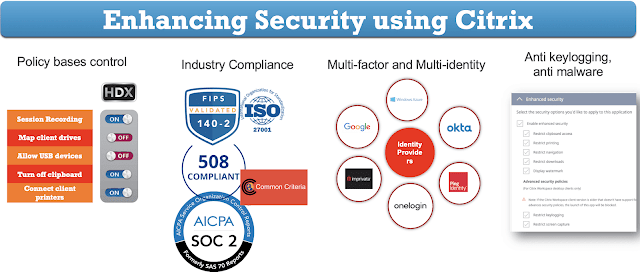
Policy Controls
Citrix provides a lot of options in granular policy controls. This ensures that administrators have an opportunity to fine-tune the environment based on the security measures which are most important to them. The security policies range from session recording, mapping client drives, allowing USB devices, turning off clipboard access, or connecting client printers. These policies can be applied from Citrix Studio or Microsoft Group Policies. There are many group policies apart from these security policies which ensure that the perfect balance of user experience and security can be maintained. These policies are really fine-grained and unlike other vendors, can really apply to the right set of users or groups in a nested way. There are some policies that come out of the box to give a good and comprehensive starting point, and also provide an opportunity to administrators to fine-tune it for the environment.
Industry Regulations
Citrix has been a choice of virtualization platform for various highly regulated industries. Many of these industries are regulated in nature hence the expectation is that solutions must comply with specific Industry Regulations. Fortunately, Citrix solutions are directly compliant with multiple industry regulations or can be used in a design that is industry-regulated. some of the common standards go like PCI DSS for the finance industry, HIPAA and HITECH for the healthcare industry, GDPR for Europe, SOX compliance for public companies, and FISMA for Government entities. While Citrix services are also compliant, there is also a big responsibility on the service provider for the right architecting of the environment.
Federation Authentication Service (FAS)
We touched on federation authentication services (FAS) in our “user experience pillar” as well. This service not only allows a seamless user experience but also provides a lot of security measures. It allows flexible and secure authentication to any app using any identity provider. It provides a single sign-on experience to any web or SaaS application or virtual app or virtual desktop with your choice of identity provider. It is a flexible and simple authentication architecture for B2B and service provider scenarios. FAS enables architectures to include Passwordless authentication.
Configuration Logging
When there are multiple administrators in any environment then it is important to know which administrator has made which changes. Configuration logging provides the exactly same capability. It records all of the admin tasks performed within the virtual app and desktop. it is very important for administrators where audit trails are required for compliance reasons. In a few regulated industries like financial services, and healthcare services we see this as a commonly asked requirement.
Multifactor Authentication
Multi-factor authentication is the other most asked security feature that is not dependent on any industry or regulation but rather has become the de-facto standard for any industry. While many of the solutions provide multifactor authentication, Citrix takes the capability one step further. Citrix can integrate with any multi-factor authentication system and provide n-factor authentication architecture. This means chaining (n-Factor) multiple authentications can be done. However, as we know that multi-factor authentication might also degrade user experience when users are already coming from a secured location like the corporate network. Citrix can intelligently sense that the incoming user connection is from which type of endpoint, location, or network condition, and based on that it can provide the required multi-factor challenge for users to log on and consume any application.
Identity Integration
Citrix provides an option to choose any identity provider. It can seamlessly integrate with Okta, PingIdentity, Google, SAML or others. Some of the basic integrations are even available directly from Citrix Gateway Services, however, for advanced integrations, Citrix ADC can be used. This capability helps a lot in the case of different mergers and acquisitions because the different entities may use different identities, and in the case of a merger, rather than moving all the users from one identity to another identity, it is quite easy to integrate all of them and provide a seamless login experience.
Session Watermarking
Few simple security controls like text-based session watermarking provide a tamper-proof identification of username, protocol, hostname, timestamp, or client IP address. This visual watermarking on the screen keeps the temptation away from copying or taking a screenshot and sharing the data unauthorisedly. If done so, then it leaves the trail back to the user who breached the information.
Anti-Screen Capture and Anti-keylogger
Citrix App protection capability secures endpoints against keylogging and screen capture malware. Up till now, we saw that Citrix provides a lot of security controls for the session, but there’s no assurance of security from the endpoints. With increasing BYO scenarios, we are seeing more and more personal devices being used for work. These devices may have malicious key loggers or screen capture malware. Citrix App Protection provides the perfect solution to increase security and fight against these factors. App Protection scrambles keystrokes and returns screenshots as black screen rendering malware ineffective. currently, this is a highly asked feature for regulated industries.
Remote Browser Isolation
In many situations, employees require access to the Internet access for non-corporate web activities. Unlike other solutions where you can either allow all block access of web pages, Citrix provides a balanced path to ensure adequate security while balancing users’ experience. Citrix Remote Browser Isolation provides a temporary, disposable browser hosted on a cloud service that safeguards the endpoint point and the endpoint network from unforeseen security threats.
Citrix can intelligently redirect internet browsing tasks to an isolated cloud-hosted web browser to enhance IT security. With the Remote Browser Isolation service, admins can provide a cloud-based, isolated web browser to their end-users. Users feel like they are accessing a local browser, but the entire experience is contained within a Citrix-managed cloud and entirely isolated from your network, removing any risk of contamination.
Summary
To summarise, as mentioned earlier, these features or enhancements are just like scratching the surface, they have a deep technology later and wide adoption rate to justify the usage of Citrix Virtual Apps and Desktop as a preferred choice for delivering virtualized apps and desktops to any device, any time and on any network. For any successful adoption, a balance of Security and Experience is a must. To know how Citrix ensures the experience, make sure to check out “enhancing the experience with Citrix“.
Please do share your thoughts and comments if you would want an explanation on any particular service or requirement.