Introduction
In recent years, many companies have moved their business processes to web applications that are accessible through the internet. However, not all applications need to be publicly accessible. Some applications are designed for internal use only. These internal web applications can provide many benefits for businesses. In this article, we will explore the benefits of using internal web applications.
Traditional Approach
There are a few ways organizations can make these internal web apps accessible to users who are not on the company network. VPN has been one of the solutions which many companies used to fulfill this challenge. However, in the longer term, VPN itself posed some challenges like scalability, network transition, and many more. More ever, with the adoption of Zero Trust security architecture, VPN-based solutions could not compete in the race.
The modern ZTNA approach
Fortunately, Citrix had an easy solution to this problem. The most widely adopted method had been to publish the internal web app through Citrix Virtual App. However, this also required additional compute and configurations. To provide a robust answer to this challenge in a Zero trust way, Citrix Secure Private Access (SPA) showed the way.
Citrix SPA allows for secure access to internal web applications without the need for a VPN. This can provide a convenient and secure way for employees to access internal applications while working remotely or on the go. By using Citrix SPA, you can ensure that your internal web applications remain secure while also providing a seamless user experience for your employees.
Simple Implementation in 1,2 and 3
The implementation of this approach is as easy as counting 1,2 and 3. The Citrix SPA solution provides many more benefits than just VPN-less access under the umbrella, however, for this post, we will consider only VPNless access.
Step 1: Connector
Once you already have the subscription to Citrix Cloud and specifically Secure Private Access, step 1 starts with deploying a ‘Citrix Connector Appliance’. As the name suggests, it’s a hardened Linux-based virtual appliance, which can be downloaded for the appropriate hosting location. It supports pretty much all hosting locations like Citrix Hypervisor, Hyper-V, ESXi, Nutanix AHV, AWS, GCP and Azure. In my lab, I have used the Azure hosting location, hence the appliance can directly be imported from the Azure Market Place. Being a Linux appliance and with a very small configuration (Standard_A2_v2), it does not make a huge impact on Azure billing. Once the connector is all set, it’s about some very easy configurations to connect and register with the Citrix Cloud Instance. Once it is done, your internal web apps are accessible through this Connector Appliance.
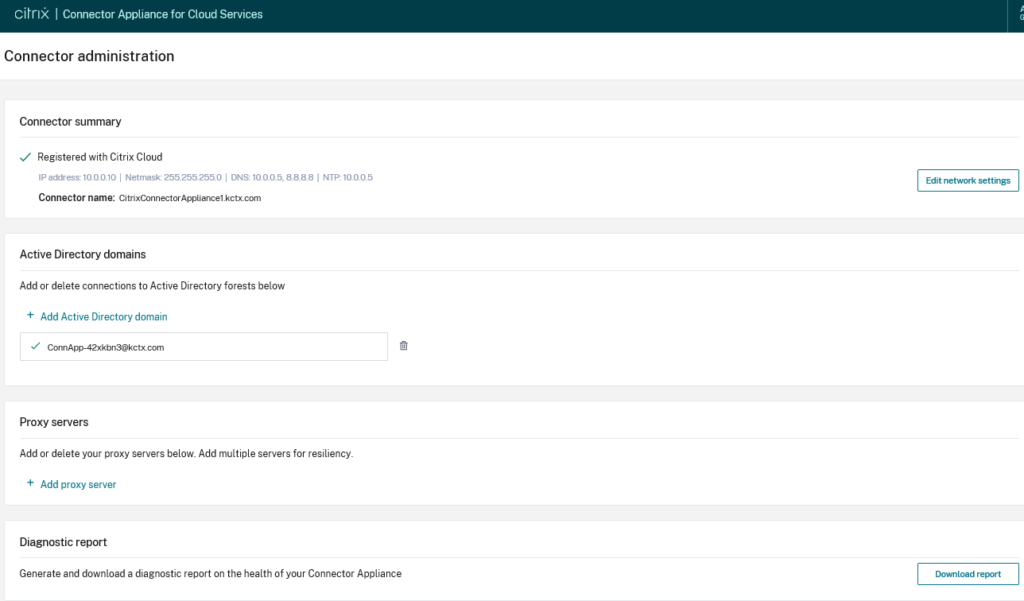
Step 2: Configure the Appliance with Security levers
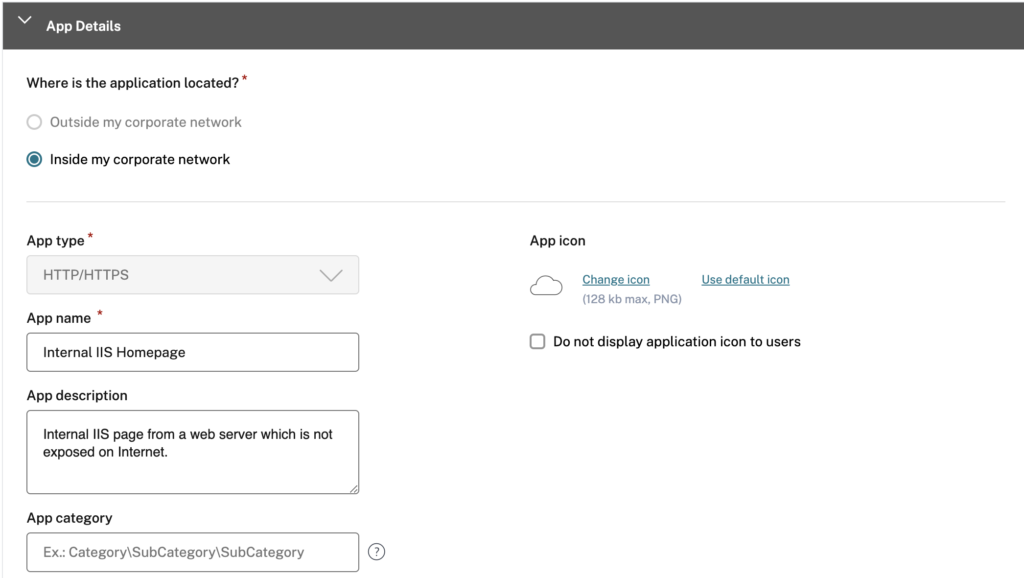
Once the connector is up and running, the next step comes in configuring the application in the Secure Private Access wizard. The wizard is very simple and intuitive. In this wizard, you just need to provide details of:
- Application Details – Inside my Corporate network
- Single Sign-on – Don’t use SSO
- App Connectivity – Validate the Connector Appliance which we have configured in Step 1
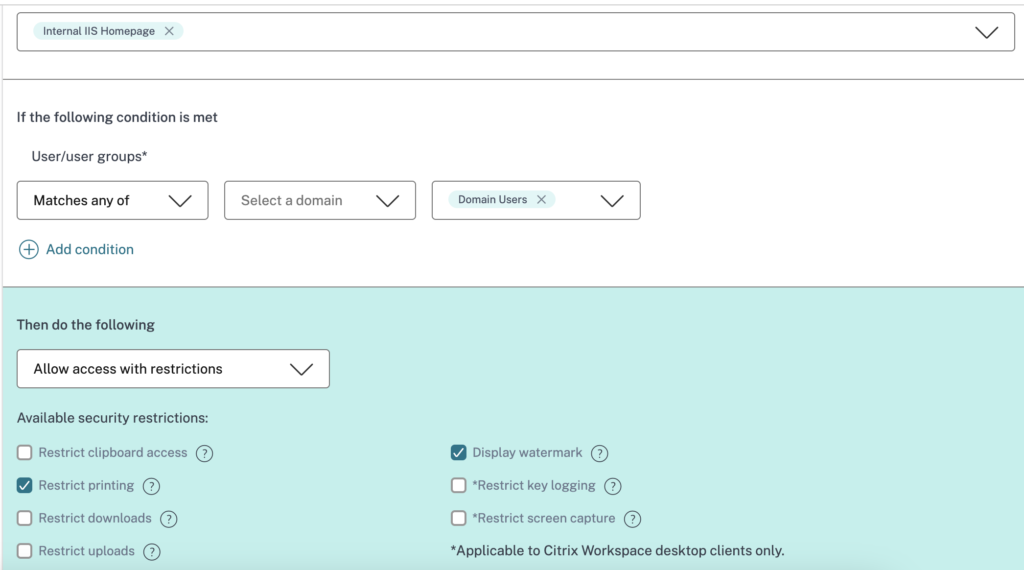
Once the app is in the Secure Private App listing, go to Access Policies and create a new access policy. In this wizard:
- Choose the application which we have created in the above step
- Provide access to the required group. If needed, add more complex conditionals like Desktop, mobile device, Geo-Location, Network location, or Device Posture check.
- To enhance security once the app is launched – play with options like restricting clipboard access, printing, downloading, uploading, display watermark or apply App Protection policies like restricted keylogging or restricted screen capture. In addition, you can force the application to open in a Remote Browser Isolation as well.
Once done, give a policy name and save the wizard.
Step 3: validate the launch on Remote Browser or Enterprise Browser
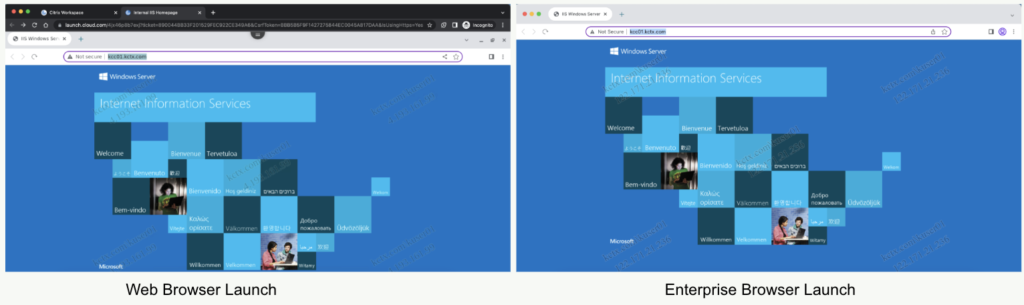
Once the above step is completed, the last step is to test the launch. Based on the configurations and the endpoint status, the launch steps might differ slightly. Like any other Citrix published application, there are really two ways to access the published resource which are Browser based Workspace App and a fully installed Workspace app.
- Launch in Workspace Web: If you have not applied any security policies, the internal app will just launch in the native web browser. However if you have applied any security policies (like watermark etc), it invokes Remote Browser within the native browser. This remote browser provides the configuration which you have chosen.
- Launch in Installed Workspace App: Once you install a workspace app, it includes a silent installation of the Citrix Enterprise browser. This browser is a chromium-based browser, which runs on the local machine and consumes resources locally. Once the internal app is launched, it invokes the Enterprise browser and includes all the security policies you have configured in the SPA Wizard. In case you have chosen a forced Remote Browser, then it invokes the Remote Isolation browser within the enterprise browser.
Conclusion
In conclusion, Citrix Secure Private Access provides a convenient and secure way for employees to access internal web applications without the need for a VPN. By using Citrix SPA, you can ensure that your internal web applications remain secure while also providing a seamless user experience for your employees. The implementation of Citrix SPA is easy and can be completed in just a few steps. Overall, Citrix SPA provides a great solution for companies looking to provide secure remote access to internal web applications.